 |
| ||||||||
Customer would like to use a certificate instead of a shared secret to authenticate the Integration Toolkit’s (ITK) Data Transfer Tool (DTT) with the Ariba applications.
There are two types of ITK Security:
- Shared Secret-Based Authentication
- Digital Certificate-Based Authentication
Digital Certificate-Based Authentication is provided because the shared secret mode of authentication is not considered secure enough to meet the stringent data security regulations imposed by certain countries. These regulations relate, particularly, to user and supplier data. In addition, certain industries and government-owned organizations require a high threshold for privacy and data security.
To ensure a completely secure exchange of the data between Ariba On-Demand Solutions and Ariba ITK, Ariba provides digital certificate-based authentication. In Ariba Spend Management solutions, which are configured for digital certificate-based authentication, a certificate authenticates upload and download requests from the Ariba ITK.
Instructions covering how to configure the Ariba application for Digital Certificate-Based Authentication appear in the current version of the Ariba On Demand Solutions Integration Toolkit Guide.
On the customers side, the DTT parameter/options file needs to have the path to the keystore that contains the public and private keys for the certificate.
Instructions for setting up a keystore and configuring the DTT parameter/options file follow:
The parameter/options file has an example of the keystore path. The keystore needs to contain the public/private keys for the certificate.
:: Enables the client certificate use for authenticating the client on the remote site.
:: The keystore pointed by this configuration has to contain the pair of public/private keys
:: for the authentication. Correct set of passwords has to be provided to access the keystore.
::
:: set clientKeystore=C:\cert\MyKeyStore.jks
:: set clientKeystorePassword=storePass
:: set clientKeyPassword=keyPass
- To create a keystore on a computer running Microsoft® Windows, you can use the following commands. Variations to this command exist, however, one example follows. The java®, "Keytool" command generates the keystore:
C:<Path to the folder you want the Keystore to reside>>keytool -genkey -alias <Name of the Keystore> -keyalg RSA -keystore <Name of the Keystore>.jks -keysize 2048 (this is user specific and can also be 1024)
Example:
D:\Data\IntegrationToolkitCertificates\cert>keytool -genkey -alias ITK -keyalg RSA -keystore MyKeyStore.jks -keysize 2048
Enter keystore password: <Enter a Password for your new Keystore> (This is the “storePass” that is set in the parameter set clientKeystorePassword= )
Re-enter new password: <Re-Enter a Password for your new Keystore>
What is your first and last name?
[Unknown]: <Enter the Name you want associated with this keystore>(John Customer)
What is the name of your organizational unit?
[Unknown]: <Enter the Name of your organizational Unit> (Ariba)
What is the name of your organization?
[Unknown]: <Enter the Name of your organization> (Ariba)
What is the name of your City or Locality?
[Unknown]: <Enter your City or Locality> (Pittsburgh)
What is the name of your State or Province?
[Unknown]: <Enter your State or Province> (PA)
What is the two-letter country code for this unit?
[Unknown]: <Enter the two-letter country code for this keystore> (US)
Is CN=JohnCustomer, OU=Ariba, O=Ariba, L=Pittsburgh, ST=PA, C=US correct?
[no]: yes - You see the following prompt. You can enter a new password or keep it the same as the keystore password. If you enter one, it is entered in the parameter/options file as set clientKeyPassword=
Enter key password for <Keystore Alias>
(RETURN if same as keystore password):
A screenshot of the commands follows in an example: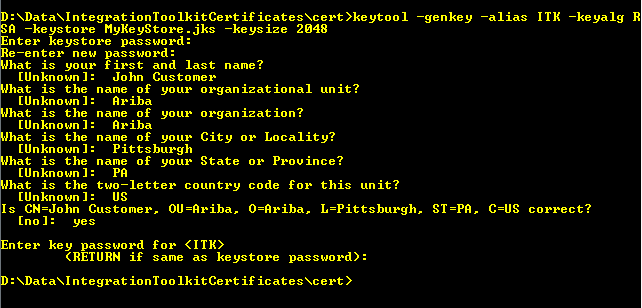
The parameters in the Parameter/Options file would, then, look like this using the current example:
set clientKeystore=D:\Data\IntegrationToolkitCertificates\cert\MyKeyStore.jks
set clientKeystorePassword=ariba123
set clientKeyPassword=ariba123 - Comment out the Shared Secret parameters:
:: set encryptionKeyPath=
:: set integrationPasswordKeyPath= - Import your certificate public and private keys to your newly created keystore.
Microsoft and Microsoft Windows are trademarks or registered trademarks of Microsoft Corporation or its subsidiaries in the United States and other countries.
Oracle and Java are trademarks or registered trademarks of Oracle Corporation or its subsidiaries in the United States and other countries.
Core Procurement > Core Administration > Integration Toolkit (ITK)
Purchasing > Services Procurement
